The Tesseract Academy was recently awarded a grant by the Alan Turing Institute to perform research on the use of Large Language Models in the creation of simulated environments for the training of Deep Reinforcement Learning algorithms.
AI and cybersecurity are two of the hottest topics right now. The global geopolitical tensions have created a sense of urgency in this area, with all big powers researching improved systems for cyber-warfare.
At the same time, AI is making the headlines everywhere. ChatGPT and the AI revolution is bringing a multitude of changes to society and the economy.
It comes to no surprise that AI and cybersecurity can be combined to create something that it’s more than the sum of its parts.
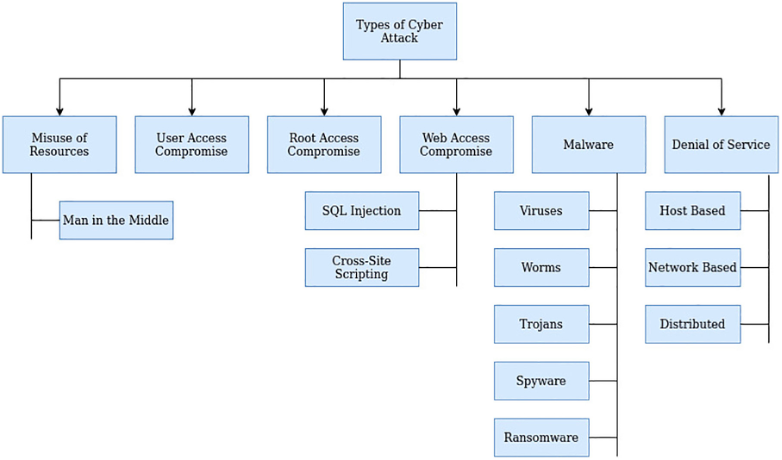
Domains of cybersecurity and machine learning (Dasgupta, 2022)
Cybersecurity and Deep Reinforcement Learning
In the domain of cybersecurity, the application of traditional defensive mechanisms often relies heavily on pre-established rules and static patterns of detection. This model, although functional, is invariably limited in its adaptability. Reinforcement Learning (RL), and especially Deep Reinforcement Learning (DRL), an advanced subset of machine learning, presents a promising alternative. Within cybersecurity contexts, RL’s innate ability to dynamically react to environmental stimuli offers a more responsive defence mechanism.
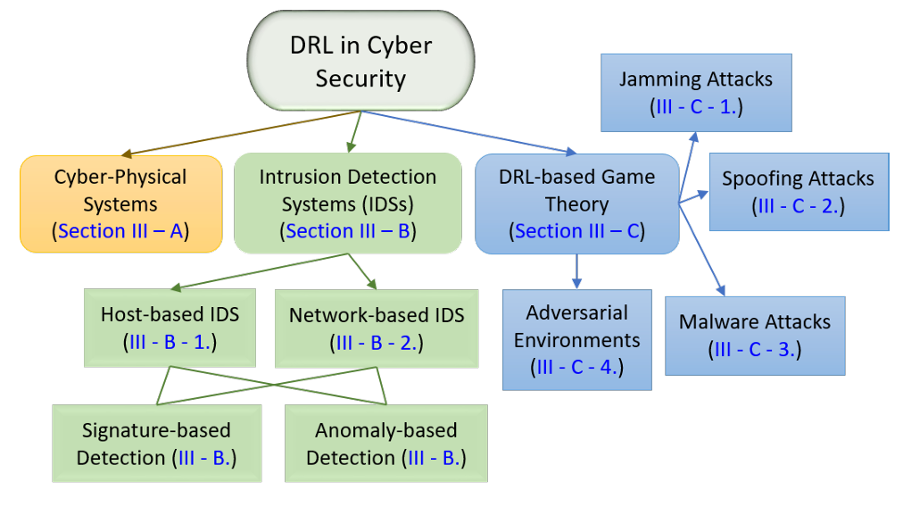
Applications of DRL in cybersecurity (Nguyen & Reddi, 2021)
Furthermore, its iterative learning process, anchored by reward-based feedback, enables the continuous refinement of defence strategies. Thus, RL could provide an adaptive framework for cybersecurity, enhancing system robustness against evolving cyber threats.
The purpose of our investigation will be to build an LLM framework that will allow the rapid creation of environments for the training of reinforcement learning models in the domain of cybersecurity.
Please get in touch for any enquiries or if you are interested in collaborating on this research.